
Overview
In 2026 my site came under significant attack, with thousands of attacks in a little more than a week. I went into hyperdrive to design and implement a comprehensive, multi-layered security infrastructure for my WordPress site, Python apps, and two servers (Apache for WordPress and nginx for my apps) under sustained cyberattack.
The solution stopped more than 5,000 login attempts in 12 days, blocked hundreds of malicious hostnames, and hardened all server access points against a sophisticated, targeted threat actor—with zero downtime to public content. 💪
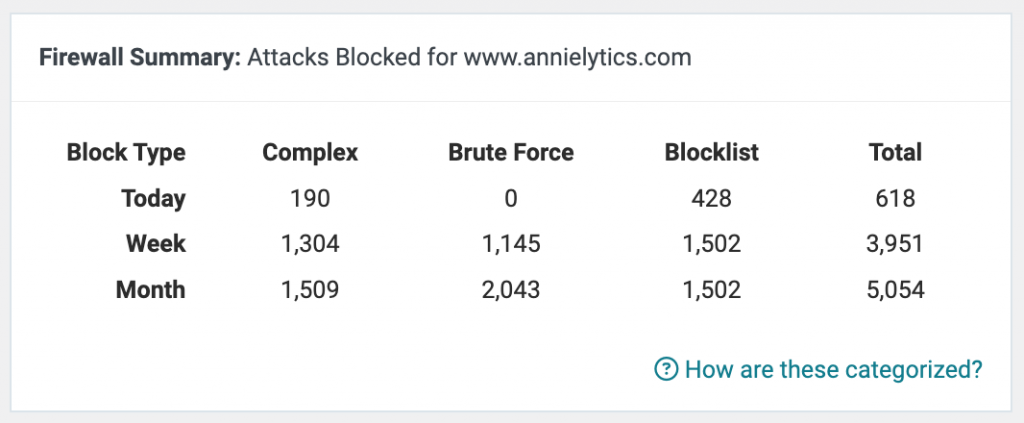
The Threat
Prior to implementation, the site was receiving approximately 445 WordPress login attempts per day across multiple attack types including brute force, complex exploits, and blocklist-matched attacks. SSH brute force attempts were also ongoing. Attack origins spanned Vietnam, Turkey, Iraq, Venezuela, the Philippines, Argentina, and Colombia, with additional evidence of coordinated activity from NYC-area IP addresses, which suggested a targeted attack rather than opportunistic threat as I live in NYC.
What I Built
WordPress Security
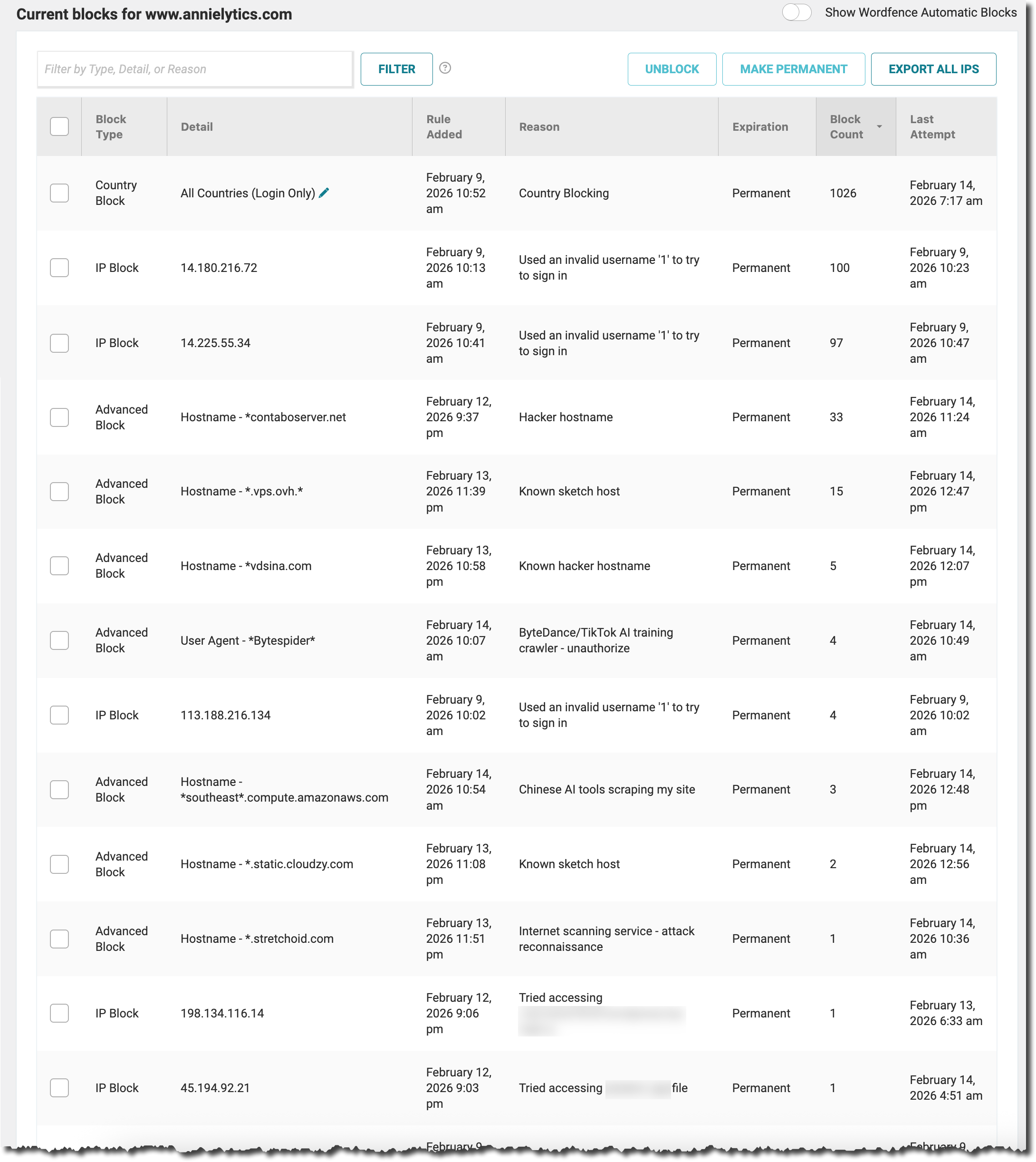
- Set up Wordfence to unlock real-time threat intelligence and country blocking.
- Configured login attempt limits (reduced from 20 to 3), 4-hour lockouts, and instant permanent blocking for commonly-attacked usernames.
- Enabled two-factor authentication and set a 20+ character admin password.
- Deployed Surfshark VPN with a dedicated IP address and restricted wp-admin access exclusively to that IP, with 2FA bypass configured to handle VPN latency.
Server-Level Blocking (nginx)
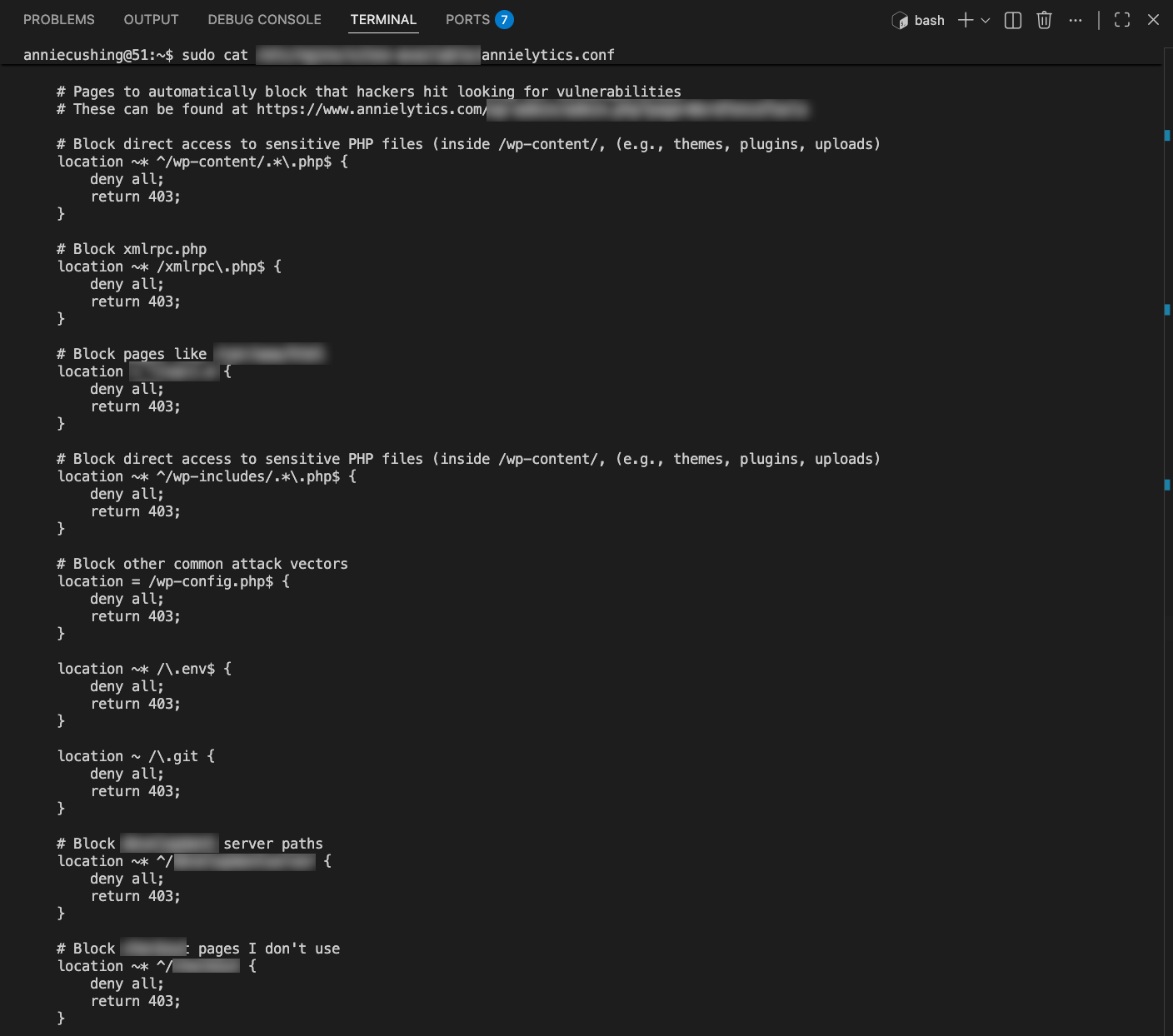
- Implemented server-level rules that stop malicious requests before they reach WordPress.
- Blocked direct access to xmlrpc.php (a primary WordPress attack vector), wp-config.php, .env files, .git directories, PHP execution in the uploads folder, RSS feeds, WooCommerce checkout paths, and path traversal attempts using absolute server paths.
Hostname-Based Blocking
- Analyzed Wordfence Live Traffic logs to identify and classify malicious hosting infrastructure.
- Created permanent custom blocks for 30+ providers including Russian VPS networks (vdsina.com), known criminal hosting (cloudzy.com, hvvc.us), residential proxy networks (Luminati/Bright Data via lum-int.io), German VPS providers (Hetzner, Contabo, OVH), internet scanners (Stretchoid, nPulse), and deliberately obfuscated hostnames.
- AI Crawler Strategy Blocked AI training crawlers (ByteDance/Bytespider, CCBot, Google-Extended, Anthropic) to protect content, while deliberately allowing GPTBot and PerplexityBot.
- GPTBot was preserved because ChatGPT citations drive traffic from the target analytics audience.
- PerplexityBot was preserved because Perplexity is heavily used by AI, data, and analytics professionals—the core readership of annielytics.com.
SSH Security & Server Hardening
- Installed and configured Fail2Ban with permanent bans after 3 failed SSH attempts.
- Confirmed root login was disabled.
- Configured SSH key authentication on all my machines for password-free access.
- Whitelisted three trusted IPs to prevent accidental self-lockout.
- Applied 251 system updates including 188 security patches.
Notable Findings
- Log analysis revealed attack sophistication beyond typical background WordPress noise.
- A Luminati/Bright Data residential proxy network was used to rotate through millions of real home IP addresses to evade blocking—a paid professional service.
- Multiple Russian VPS servers from the same provider appeared in coordinated waves. 🪆
- An unauthorized security audit was submitted to Turaco Labs ThreatView, meaning someone entered the site URL into a vulnerability-scanning service to identify weaknesses.
- Cloudzy hosting—a known infrastructure used by ransomware groups and APTs—was also observed probing the site. 🥷
Results
- All 5,000+ documented attack attempts blocked (in a 12-day period).
- Zero successful unauthorized logins or intrusions.
- Admin panel accessible only via whitelisted VPN IP.
- All identified attack vectors eliminated at the server level.
- Password-free SSH authentication configured across all machines.
- Comprehensive attack evidence documented for potential law enforcement use.
- Public blog content remained 100% accessible to legitimate visitors throughout the entire implementation.
Skills Demonstrated
- Apache server administration
- Nginx server configuration
- WordPress security
- Network security analysis
- SSH hardening
- MySQL forensic queries
- Fail2Ban setup
- VPN configuration
- Defense-in-depth architecture
- Threat modeling
- Attack pattern recognition
- MFA setup for all services